Before we start: Donemax Data Eraser is a securely SSD disk wiping program. It can help in securely and permanently destroying data from SSD, making data recovery be impossible. It supports to shred files on SSD, wipe entire SSD, wipe free disk space of SSD, etc.
PAGE CONTENT:
Whether you're planning to sell, donate, or dispose of your SSD, securely destroying the data it holds is essential. Unlike traditional hard drives (HDDs), SSDs have a unique architecture that makes standard data-wiping techniques ineffective or insufficient. If you leave remnants of data behind, sensitive information such as passwords, financial records, and personal documents can be recovered - even after deletion. This article provides a deep dive into how SSDs store data, why secure deletion is challenging, and the most effective ways to destroy SSD data for good.
Why Secure SSD Data Destruction Matters?
In today's data-driven world, simply "deleting" a file or "formatting" a drive isn't enough. When files are deleted, only the pointers to their locations are removed - not the data itself. This is especially true for SSDs, where data can persist despite logical deletions. Here's why securely destroying SSD data is critical:
- Prevent Identity Theft: Old files may contain personal data, login credentials, or sensitive corporate documents.
- Regulatory Compliance: Laws such as GDPR, HIPAA, and PCI DSS require the secure disposal of sensitive data.
- Safe Recycling or Resale: Before handing over your SSD to someone else, it’s crucial to ensure no trace of your data is left behind.
Understanding How SSDs Work:
To securely destroy data on an SSD, you first need to understand its internal workings. SSDs do not use spinning disks and magnetic platters like HDDs. Instead, they use NAND flash memory chips and a controller that manages data access and wear-leveling.
Key Architectural Features:
- Wear-Leveling Algorithms: To avoid wearing out specific memory blocks, SSDs constantly move data around. This makes it difficult to know exactly where a piece of data is stored at any given time.
- TRIM Command: Modern operating systems use the TRIM command to mark deleted blocks for future overwriting. However, TRIM doesn't immediately delete the data—it only signals that the block can be reused.
- Over-Provisioning: SSDs reserve extra space for controller operations, which may be hidden from the user and software tools. Some data could remain in this space, even after deletion.
- Because of these factors, conventional data erasure techniques that work for HDDs (e.g., overwriting data multiple times) are unreliable for SSDs.
The Risks of Improper SSD Data Deletion:
Failing to securely delete your SSD data opens the door to a number of risks, especially if the drive falls into the wrong hands.
Data Recovery Threats:
- Freeware Recovery Tools: Even freely available tools like Donemax Data Recovery, Recuva or PhotoRec can recover deleted data if the drive hasn't been securely wiped.
- Advanced Forensics: Sophisticated recovery tools used by cybercriminals or forensic experts can retrieve data from SSDs - even after basic deletion.
Real-World Incidents:
- Studies have shown that used SSDs sold on marketplaces like eBay often contain recoverable personal data. One study by the University of Hertfordshire found that over 40% of used drives sold online still contained sensitive data.
The takeaway? You can't rely on just deleting or formatting an SSD. You need specialized tools or processes.
What Doesn't Work for SSDs?
Before jumping into the correct techniques, it's important to know which ones are not effective:
1. Standard File Deletion
Deleting files through the OS (Recycle Bin or Trash) only removes file references - it doesn't wipe the data.
Learn how to recover deleted/formatted or lost data from a SSD >>
2. Quick or Full Format
Quick format removes metadata only. Full format may write zeros in some cases, but SSDs often bypass these writes due to wear-leveling.
3. Traditional Overwriting Tools
Tools like DBAN or CCleaner's Drive Wiper, which overwrite the drive multiple times, are designed for HDDs and don't account for SSD-specific behaviors like over-provisioning and wear-leveling.
How to Securely Destroy Data on an SSD?
Now that we know what doesn't work, let's focus on the methods that do.
Method 1. Use Manufacturer Tools (Recommended for Most Users)
SSD manufacturers often provide dedicated software tools that are designed to securely erase every bit of data on their drives. These tools send low-level firmware commands, such as "Secure Erase" or "Sanitize," which directly access the SSD controller to erase data in all blocks, including those that are hidden from the operating system.
Benefits of Manufacturer Tools:
- Specifically optimized for the drive
- Reliable and easy to use
- Reduces chance of user error
- Typically free to download
Steps for Secure Erase Using Manufacturer Tools:
Example: Samsung Magician Tool
- Download and install Samsung Magician from the official site.
- Open the program and select your SSD from the list of available drives.
- Navigate to the "Data Management" tab and select "Secure Erase."
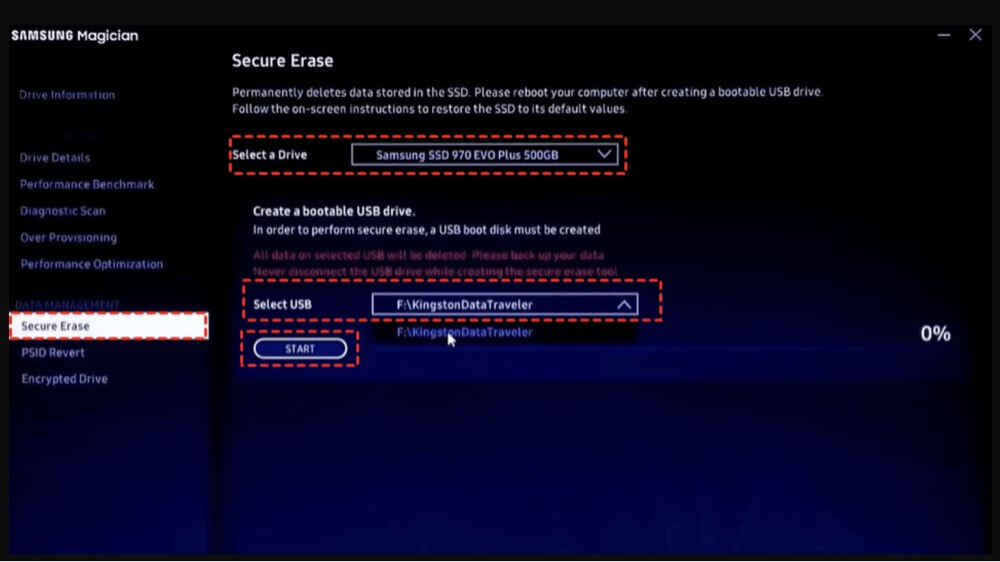
- You may be prompted to create a bootable USB drive. Follow the wizard to prepare this.
- Restart your computer and boot into the secure erase environment using the USB.
- Follow the on-screen instructions to erase the SSD completely.
💡 Caution: Make sure to back up all important files. The Secure Erase process will make data completely unrecoverable.
Other popular tools:
- Intel SSD Toolbox (Windows) – Offers a full-drive secure erase function.
- Crucial Storage Executive – Includes a "Sanitize Drive" tool that resets the SSD to its factory state.
- SanDisk SSD Dashboard – Also includes a secure erase feature under the "Tools" tab.
Method 2. Use Third-Party Tools with Secure Erase Capabilities
If you're working with a brand that doesn't provide its own utility - or you want more control - several trusted third-party solutions are available.
No.1 Donemax Data Eraser (Highly Recommended)
Donemax Data Eraser is one of the best data erasure programs for SSDs. It can securely and permanently erase data from SSDs, HDDs, USB flash drives, digital cameras, SD cards, etc. Once the data is erased by Donemax Data Eraser, the data is lost for good, no trace left behind. It offers several data erasure standards including HMG Infosec Standard 5, NIST 800-88, Peter Gutmann's algorithm, DoD 5220.22-M, U.S. Army AR380-19, DoD 5220.22-M ECE.
Steps:
1. Download and install Donemax Data Eraser.
2. Open Donemax Data Eraser, choose Erase Hard Drive mode. Then select the SSD.
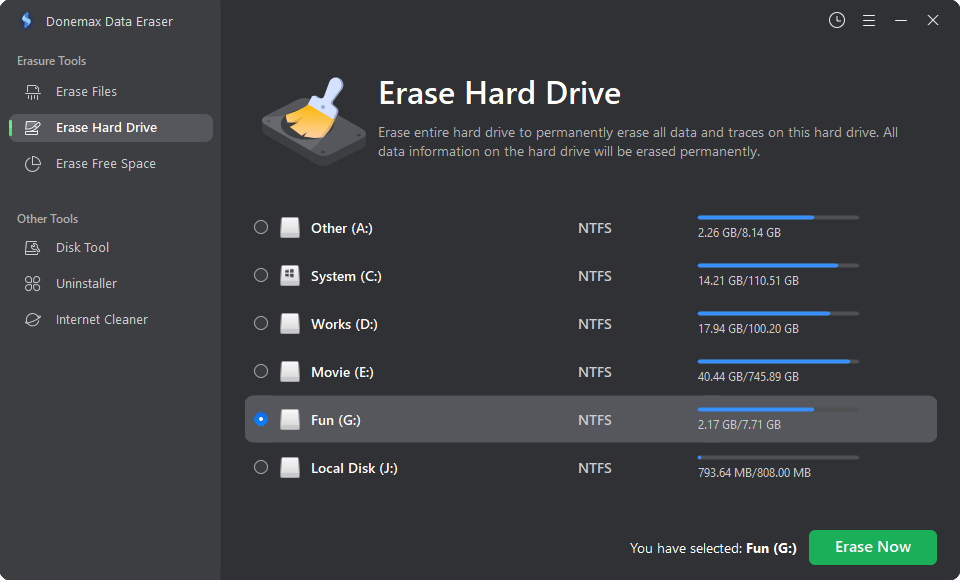
3. Click on Erase Now button to wipe the SSD. All data including existing data, deleted/formatted/lost data stored on the SSD will be erased permanently, can't be recovered by any method.
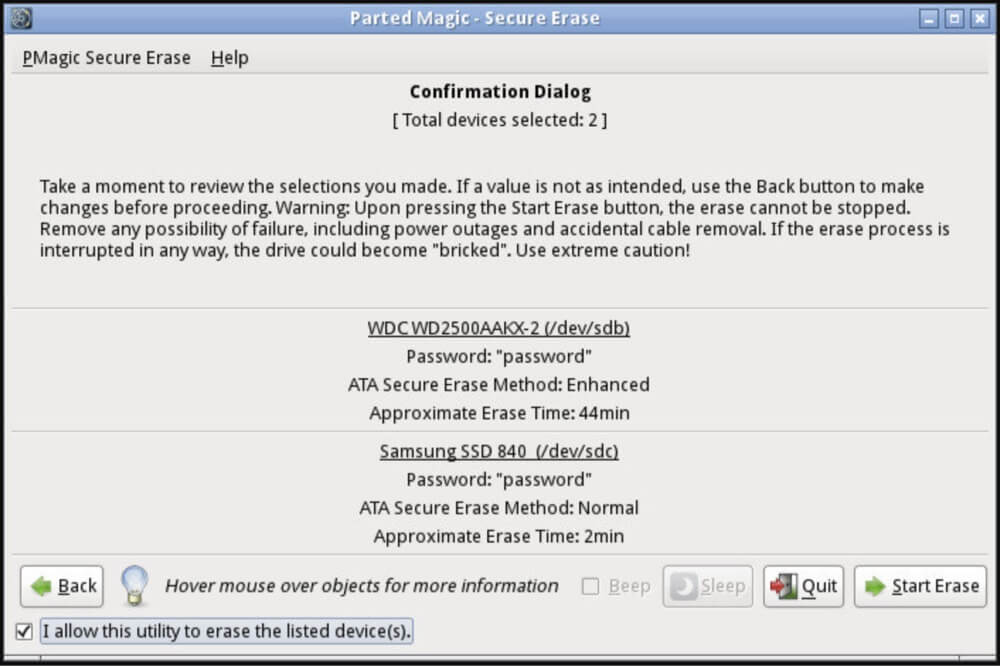
NO.2 Parted Magic
Parted Magic is a bootable Linux-based environment that offers secure erase features for both SSDs and HDDs. It supports ATA Secure Erase and Enhanced Secure Erase, both of which are effective in SSDs.
Steps:
- Purchase and download the ISO from Parted Magic's official site.
- Create a bootable USB stick or CD using tools like Rufus or Etcher.
- Boot into the Parted Magic environment.
- Navigate to the "Erase Disk" tool and choose "ATA Secure Erase."
![Securely Destroy Data on SSD]()
- Confirm the drive and execute the process.
💡 Tip: If the SSD is in a frozen state, put the system to sleep and wake it up again - this usually unfreezes the drive.
NO.3 Blancco Drive Eraser
Blancco is a commercial-grade solution used by IT departments for compliance-based drive erasure. It meets standards like NIST 800-88 and DoD 5220.22-M, making it ideal for enterprise environments.

Method 3. Encryption + Key Destruction (Data Obfuscation Strategy)
When secure erase or manufacturer tools aren't an option - for example, if the drive is partially corrupted - another approach is encrypting the entire drive and then deleting the encryption key. This doesn't remove the data physically but renders it unreadable and practically impossible to recover.
Steps:
- Encrypt the SSD
- On Windows, use BitLocker to encrypt the entire drive.
- On Mac, enable FileVault in System Preferences.
- Delete the Encryption Key
- In BitLocker, disable encryption and remove the recovery key from the system and backups.
- In FileVault, wipe the keychain and disable the encryption manually.
- With VeraCrypt, deleting the key file (if used) ensures data becomes inaccessible.
Why It Works:
Without the decryption key, even if the NAND cells still contain bits of data, they appear as meaningless gibberish to any forensic software.
💡 Note: This method is best used for non-functional drives where software-based secure erase is no longer possible.
Method 4. Physical Destruction: Last Resort for Total Assurance
When software-based solutions aren't enough - like when the drive is physically damaged or inaccessible - physical destruction becomes necessary.
When to Physically Destroy:
- The drive has failed and cannot be wiped.
- You want guaranteed, irreversible data destruction.
- You are disposing of highly sensitive or classified data.
Effective Physical Destruction Techniques:
- Dismantling the SSD
- Open the SSD casing.
- Locate the NAND flash chips (rectangular black chips on the board).
- Destroy the NAND Chips
- Use a hammer or drill to shatter the chips.
- Alternatively, use industrial shredders (available from e-waste recyclers).
- Incineration or Acid Baths (Extreme Measures)
- Incineration and acid treatments are used by government agencies but aren’t practical for consumers.
⚠️ Warning: Just drilling a few holes in the SSD shell is not enough. You must destroy the actual memory chips on the PCB.
Best Practices for Secure SSD Data Destruction
1. Backup Before You Wipe
Make sure you have transferred any important files before erasing the drive.
2. Verify Erasure
Use disk analysis tools like Hex editors or forensic software to verify that the data is no longer recoverable.
3. Stay Compliant
If you're handling regulated or business-critical data, ensure the erasure method meets legal standards (e.g., NIST 800-88 Rev. 1, ISO/IEC 27040).
4. Recycle Responsibly
After data destruction, recycle your SSD at certified e-waste centers to reduce environmental impact.
Conclusion
SSDs require special handling when it comes to secure data destruction. Due to their internal architecture, standard deletion and overwriting methods often fail to fully remove data. Fortunately, tools provided by SSD manufacturers, third-party secure erase software (such as Donemax Data Eraser), and encryption strategies offer reliable solutions.
When all else fails, physical destruction of the NAND chips ensures complete data elimination. Whichever method you choose, make sure it aligns with the sensitivity of your data, your technical skill level, and any legal or regulatory requirements.
By following these practices, you’ll not only protect your data but also contribute to responsible device disposal in a digital age where privacy is everything.


Donemax Data Eraser
One of the best data erasure programs for permanently erase data from PC, Mac, HDD, SSD, USB drive, digital camera and other devices. Once the data is erased, it is lost for good, cannot be recovered by any method.
Related Articles
- Apr 07, 2025How to Recover Data from SATA SSD? [3 Methods]
- Nov 21, 2024Fix Bad Sectors on SSD Without Losing Data
- Jul 24, 2024How to Fix SanDisk Portable SSD Not Working on Mac?
- Feb 24, 2025Reset or Erase SSD with Diskpart (Command Prompt Tool)
- Feb 05, 20256 Solutions to Fix Can't Format SSD in Disk Management
- Nov 15, 2024What Is the Best SSD Repair Tool? Here Are 7 SSD Repair Tools

Christina
Christina is the senior editor of Donemax software who has worked in the company for 4+ years. She mainly writes the guides and solutions about data erasure, data transferring, data recovery and disk cloning to help users get the most out of their Windows and Mac. She likes to travel, enjoy country music and play games in her spare time.

Gerhard Chou
In order to effectively solve the problems for our customers, every article and troubleshooting solution published on our website has been strictly tested and practiced. Our editors love researching and using computers and testing software, and are willing to help computer users with their problems