PAGE CONTENT:
Are you getting a new computer or getting rid of an old hard drive? Don't throw it away yet - keeping your info safe is more important than ever! Think of your hard drive as a treasure box with private and sensitive data. Secure data destruction requires more than erasing files or changing their format; you must master digital forensics.
We will keep your secrets safe by exploring this article's exciting world of data erasure. We know how to ensure your data is so erased that no one can return it. It includes using software tools to break into virtual safes and destroy real ones.

The Deleted and Formatted Data Is Not Gone Forever
A common misconception is that merely removing files or formatting a hard disk will ensure that data is removed permanently. However, this is not the case whatsoever. The operating system will indicate the space as accessible for new data when you remove a file; however, doing so will not eliminate the information in the file. These "deleted" files can be recovered with the help of specialized software. It is necessary to overwrite the information on the hard drive to delete data completely.
Popular Data Overwriting Methods
a. Standard Overwrite Methods:
Utilizing conventional overwrite methods is one of the most popular approaches for the secure deletion of data. Methods like these include repeatedly replacing the already present data with characters chosen at random or with specific patterns. Regarding overwriting, the Department of Defense 5220.22-M and the NIST 800-88 propose a minimum of three passes or more.
b. Gutmann Method:
Thirty-five passes of overwriting data are required for the Gutmann method, named after its originator, Peter Gutmann. Even though it could appear excessive for contemporary hard drives, it was developed to guarantee data destruction on earlier technologies. Even though others believe fewer passes are adequate for today's drives, the Gutmann method is an all-encompassing strategy.
Methods for Destroying Data on A Hard Drive
Method 1. Data Destruction Software
Some software solutions are available, each providing user-friendly interfaces and various overwrite methods to simplify data deletion. Donemax Data Eraser, DBAN (Darik's Boot and Nuke), Eraser, and KillDisk are among the most popular choices. These programs frequently enable users to generate bootable USB devices or CDs for offline data destruction. It enhances security by allowing users to circumvent the operating system that is currently installed.
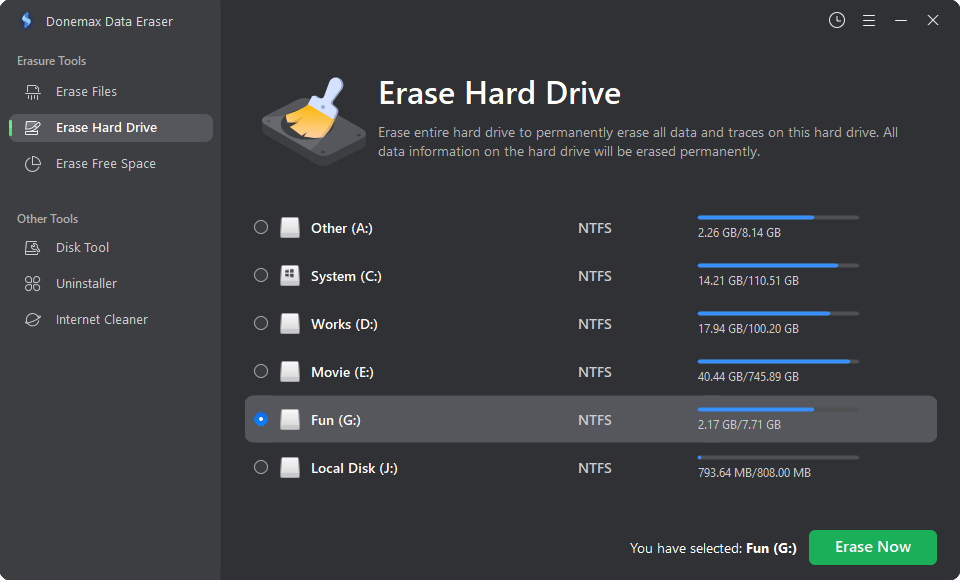
For example, both Windows users and Mac users can use Donemax Data Eraser to destroy data stored on a hard drive and make data recovery be impossible.
Donemax Data Eraser
- Easy-to-use data erasure software, 100% safe.
- Certified data erasure standards including Peter Gutmann, U.S. Army AR380-19, DoD 5220.22-M ECE, etc.
- Once the data is erased by Donemax Data Eraser, the data is lost forever, can not be recovered by any method.
With Donemax Data Eraser, anyone can wipe a hard drive and make data be unrecoverable:
Step 1. Open Donemax Data Eraser, then choose Erase Hard Drive.
Step 2. Select the hard drive and click on Erase Now button to permanently erase all data stored on the hard drive, beyond the scope of data recovery.
Method 2. Encryption and Secure Deletion
Encrypting the data on your hard disk is an effective preventative strategy that should be considered before ever considering the possibility of physical destruction. Tools that encrypt the entire disk, such as BitLocker for Windows or FileVault for macOS, ensure that even if an unauthorized person has physical access to the drive, In the absence of the encryption key, no one can decipher the information.
The deletion of individual files can be accomplished securely by utilizing secure deletion applications such as Donemax Data Eraser, BleachBit or CCleaner. With the help of these tools, the file is overwritten with random data, making it extremely difficult or practically impossible to restore.
Method 3. Physical Destruction
The physical destruction of the hard disk is a completely foolproof procedure for individuals who emphasize absolute assurance. It entails rendering the drive unworkable to guarantee that no data recovery strategies may be utilized. The following are some methods of creating physical destruction:
a. Shredding:
To render the hard drive irreparable, the process of Shredding entails the utilization of specialized equipment to shred the hard drive into little fragments physically. This procedure is quite prevalent when it comes to professional data destruction services.
b. Drilling:
Drilling holes through the platters of the hard disk is yet another way that functions effectively. It causes the platters to become damaged, which makes it extremely difficult to recover the data. On the other hand, it is necessary to drill through each platter to guarantee total devastation.
c. Degaussing:
When degaussing, a powerful magnetic field is used to destroy the magnetic domains on the hard drive, ultimately erasing the data. Although it is an excellent solution, this technique is more frequently utilized for storing magnetic tapes than for current hard drives.

Conclusion:
To sum up, making sure that data on a hard drive is deleted permanently takes several steps. Using software-based methods, encryption, and physical destruction is the best way to keep private information safe. Your needs and security needs will determine which way is best for you, or you can use a mix of them. The main goal is to protect privacy and stop anyone from getting private information without permission, no matter the method used. By following these tips, you can be sure you won't lose any private data when you get rid of old hardware or storage devices.
Related Articles
- May 10, 2024How to Wipe An USB Flash Drive on Windows 11?
- Jan 12, 2024How to Wipe NVMe SSD?
- Feb 21, 20252025 Best SD 6 Card Formatter: Format/Wipe/Repair SD Card
- May 06, 2024How to Factory Reset Gopro HERO12 Black Before Selling or Donating It?
- Jun 05, 2024How to Reset Microsoft Surface to Its Factory Settings?
- Jan 27, 2024How to Execute Unrecoverable Delete on Windows/macOS/External Storage Device?

Steven
Steven has been a senior writer & editor of Donemax software since 2020. He's a super nerd and can't imagine the life without a computer. Over 6 years of experience of writing technical solutions and software tesing, he is passionate about providing solutions and tips for Windows and Mac users.

Gerhard Chou
In order to effectively solve the problems for our customers, every article and troubleshooting solution published on our website has been strictly tested and practiced. Our editors love researching and using computers and testing software, and are willing to help computer users with their problems